Cybersecurity and Compliance is Important for All Companies
If your company has regulatory compliance requirements, please read on. But even if it doesn’t – you should still read this.
What is IT Compliance?
IT Compliance means conforming to a set of rules, policies, standards or laws for your company’s specific industry for the protection of sensitive information and IT resources. Examples of which entities would require compliance include federal and state laws, industry regulations, contractual obligations and insurance policy requirements.
You may be surprised to know that all businesses are regulated. Besides the common regulations for HIPAA (medical record privacy) and PCI (credit card processing), all states have data breach notification laws. Many states also have laws protecting the private information of customers, including social security numbers, driver’s license numbers and credit card numbers.
You may think, “We do not collect any of that information so we have nothing to protect.” Are you sure? And can you prove it if your company was investigated? For example, there was a known case where a former CFO had created a spreadsheet of all the employees’ social security numbers and bank account numbers so he could easily access the information and not have to look them up one by one in a secured database. The current CFO did not do this, but the spreadsheet still existed on his workstation and even included the CEO’s personal information!
So even though your company may not have any particular regulatory laws or compliance standards that are mandated by industry, the confidence to declare and prove that your company does not have unsecured personal information is a valuable asset.
Law, Regulation or Framework
IT Compliance can be organized at three different levels.
Law – The most absolute of compliance regulations have been made into Laws (or Acts). Any industry governed by these laws must not only safeguard their sensitive data, but must also be able to prove that the data is secure and that they are actively and proactively ensuring that their data is secure. Examples of regulatory laws include HIPAA (healthcare), GLBA (financial), FISMA (federal agencies), CCPA (California consumers), SOX (corporate governance), ITAR (US defense sales and services)
Rules – Although not laws, many industries have strict rules that they must adhere to and in most cases require independent audit and certification. Examples of industry rules include PCI-DSS (credit card privacy), DFARS and CMMC (US defense industry), FDIC (banking), HIPAA Security Rule (electronic health industry privacy), Title 21 CFR Part 11 (electronic records/signatures for biotech)
Frameworks – Neither laws, nor rules, frameworks are broad (and detailed) scopes of IT security concepts that many industries outline and define to assist with creating effective IT policies and procedures to secure data and IT systems. Examples of frameworks include NIST CSF (cybersecurity framework), NIST 800-53 (US federal information system privacy controls), NIST 800-171 (controlled unclassified information for non-federal information systems), ISO 27001 (international standard for information security) and ITSM (security framework for IT service providers).
What does my company need to do?
All companies, whether or not they are governed by laws, rules or frameworks should give some basic thought to their own cybersecurity standards. Statistically, businesses of all sizes are being actively targeted by criminals or malicious entities. A proper cybersecurity plan includes three co-equal areas of security compliance:
- Policies (a written statement of the company’s general stance on IT-related subjects, such as passwords, internet access, backups, etc.)
- Procedures (more specific details about how things are performed, such as which backup or antivirus applications are implemented, how a terminated employee is offboarded, etc.)
- Evidence (how your company documents changes to policies and procedures or deviations, exceptions and violations of security)
How Infinity Networking can help your company
Here is a list of the ways we can help your company attain proper cybersecurity standards, maintain those standards and create ongoing assurances that your company’s IT security is working and up-to-date.
Get the Basics in Place
- Your company should have a good antivirus application installed on all workstations, laptops and servers
- Your servers and critical workstations should be backed up or imaged regularly and the backups should be tested on a regular basis
- All of the operating systems on your workstations and servers should have the latest security patches and service packs
- Your company’s network should have a commercial-grade firewall between it and the internet
- You should know who is accessing your network data and remove anyone who is not authorized
Infinity Networking’s Managed IT Services is a valuable asset for your company to maintain a healthy IT infrastructure. Get more information about Managed IT Services.
NIST CSF (Cybersecurity Framework)
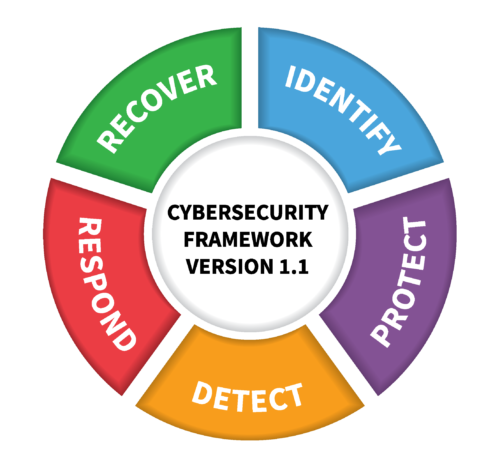
The NIST CSF has been adopted and used by many agencies and organizations because of its high-level, streamlined approach to cybersecurity. The NIST CSF has five components:
- Identify – Hardware, software and data should be identified and located
- Protect – IT systems should be protected by firewalls, antivirus, backups, etc.
- Detect – IT systems should be scanned or audited regularly to find changes or intrusions
- Respond – There should be a procedure in place to respond to any security breaches or intrusions into an IT system and report/record the incident
- Recover – In the event of a breach of security or data loss, there should be a procedure in place to recover lost data and remedy any vulnerabilities
When all five of these components are properly addressed, a company can be assured that they have a strong foundation of effective cybersecurity policies and procedures.
Infinity Networking’s Network Security Assessment is based on the NIST CSF and will run an automated scan of your network’s resources to identify the security features you have enabled as well as any issues that should be addressed. We can also assist you in creating a remediation plan to fill the holes.
Specialized Compliance Standards
In addition to the general NIST CSF framework, Infinity Networking can also assist in the scanning, detection, remediation and documentation for more specific compliance requirements such as:
- CMMC (Cybersecurity Maturity Model Certification)
- GDPR (General Data Protection Regulation)
- HIPAA (Health Insurance Portability and Accountability Act)
- PCI-DSS (Payment Card Industry Data Security Standard)
- Cyber Insurance
- Microsoft Cloud Services (Office 365, Teams, SharePoint, OneDrive, Azure)
SPECIAL OFFER
If you would like a comprehensive, detailed security scan of your company’s network, including the identification of personally identifying information (PII), network security settings and external access testing, we are offering a one-time $300 service which includes the configuration and implementation of the network scan, the creation of customized reports and a detailed remediation plan to address any problems.
In addition, if you would like to have ongoing, monthly scans of your network or if you have a specific compliance requirement listed above, we will apply the one-time scan fee to your first month’s charges for our specialized Compliance Manager application. This service is installed at your location and automatically runs on a monthly basis, providing you with regular detailed reports that can be used as evidence for audits and requests for proof of compliance.
Please contact us if you have any questions, would like to see a demo or would like to view samples of the security reports. We can also discuss the next steps needed to implement a comprehensive Security Scan for your company.



