In today’s rapidly evolving business landscape, a reliable and secure computer network is the backbone of any successful enterprise. Whether you’re a small startup or a well-established corporation, the effectiveness of your corporate computer network directly impacts productivity, collaboration, and overall business success. In this article, we’ll explore some general best practices for business owners to ensure they have a robust and secure computer network.
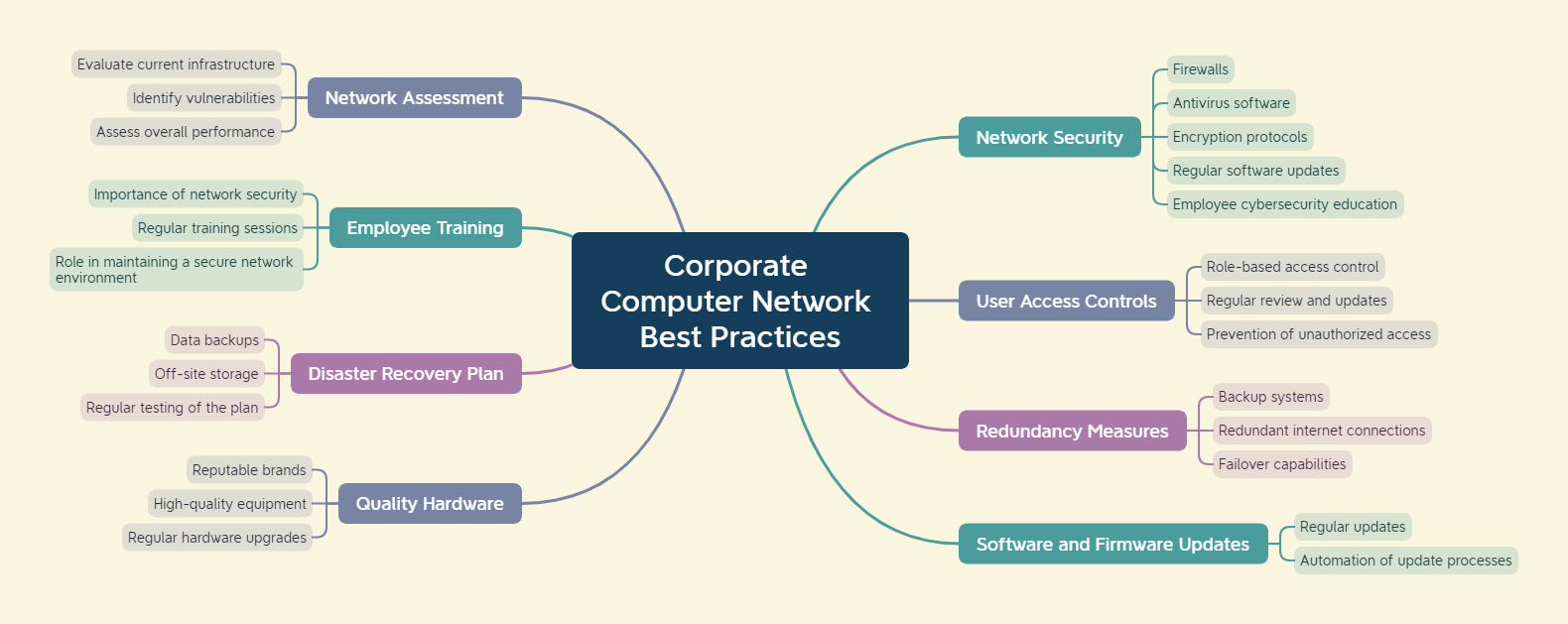
- Conduct a Network Assessment: Before implementing any changes or upgrades, it’s essential to conduct a thorough network assessment. This involves evaluating the current infrastructure, identifying potential vulnerabilities, and assessing overall performance. This initial step provides a solid foundation for planning improvements and helps prevent any unforeseen issues down the line.
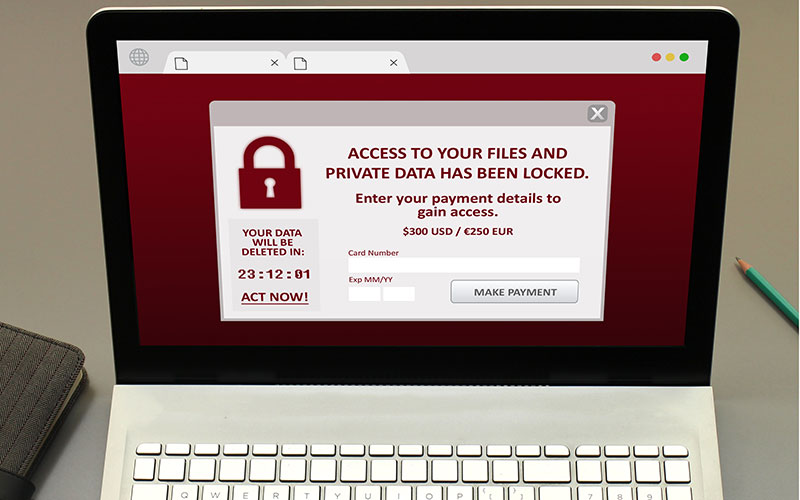
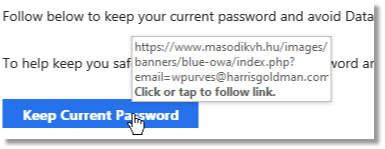
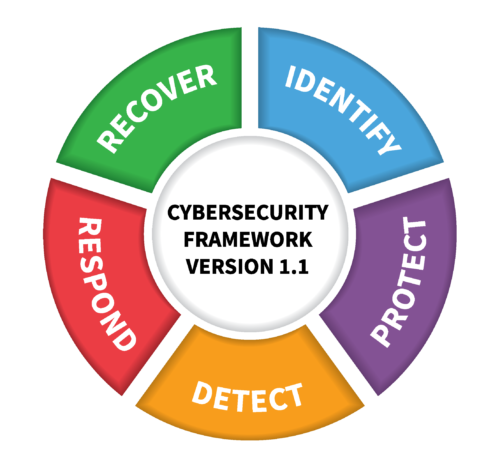
- Prioritize Network Security: Security should be a top priority when managing a corporate computer network. Implementing robust security measures helps protect sensitive data, client information, and your company’s reputation. Utilize firewalls, antivirus software, and encryption protocols to safeguard against cyber threats. Regularly update and patch software to address potential vulnerabilities and ensure that employees are educated on cybersecurity best practices.
- Establish User Access Controls: Limiting access to sensitive data is crucial for maintaining the integrity of your network. Implement a role-based access control system that grants employees the appropriate level of access based on their responsibilities. Regularly review and update user permissions to align with organizational changes and to prevent unauthorized access.
- Implement Redundancy Measures: Minimize downtime and ensure business continuity by implementing redundancy measures. This includes backup systems, redundant internet connections, and failover capabilities. By having backup solutions in place, you can quickly recover from hardware failures, minimizing the impact on productivity.
- Regularly Update Software and Firmware: Outdated software and firmware can be a significant security risk. Regularly update all network devices, including routers, switches, and servers, to ensure they have the latest security patches and performance improvements. Automate update processes whenever possible to streamline this essential maintenance task.
- Invest in Quality Hardware: The quality of your network hardware directly influences its reliability and performance. Invest in reputable brands and high-quality equipment that can handle the demands of your business. Regularly upgrade hardware to keep pace with technological advancements and to ensure compatibility with the latest software.
- Implement a Disaster Recovery Plan: Prepare for unforeseen events by developing a comprehensive disaster recovery plan. This should include regular data backups, off-site storage solutions, and a step-by-step guide for restoring operations in the event of a disaster. Regularly test your disaster recovery plan to identify and address any potential shortcomings.
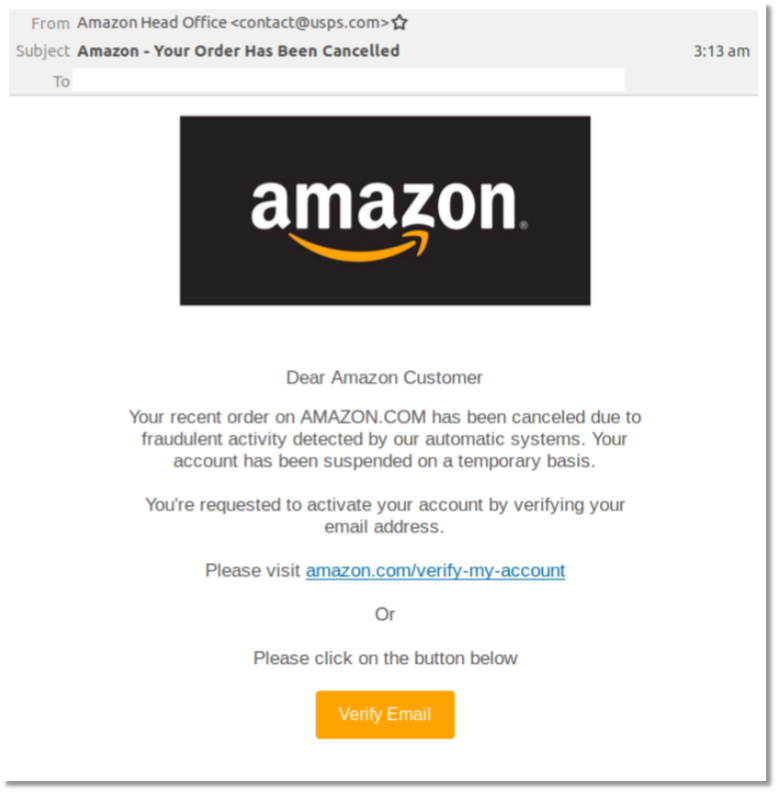
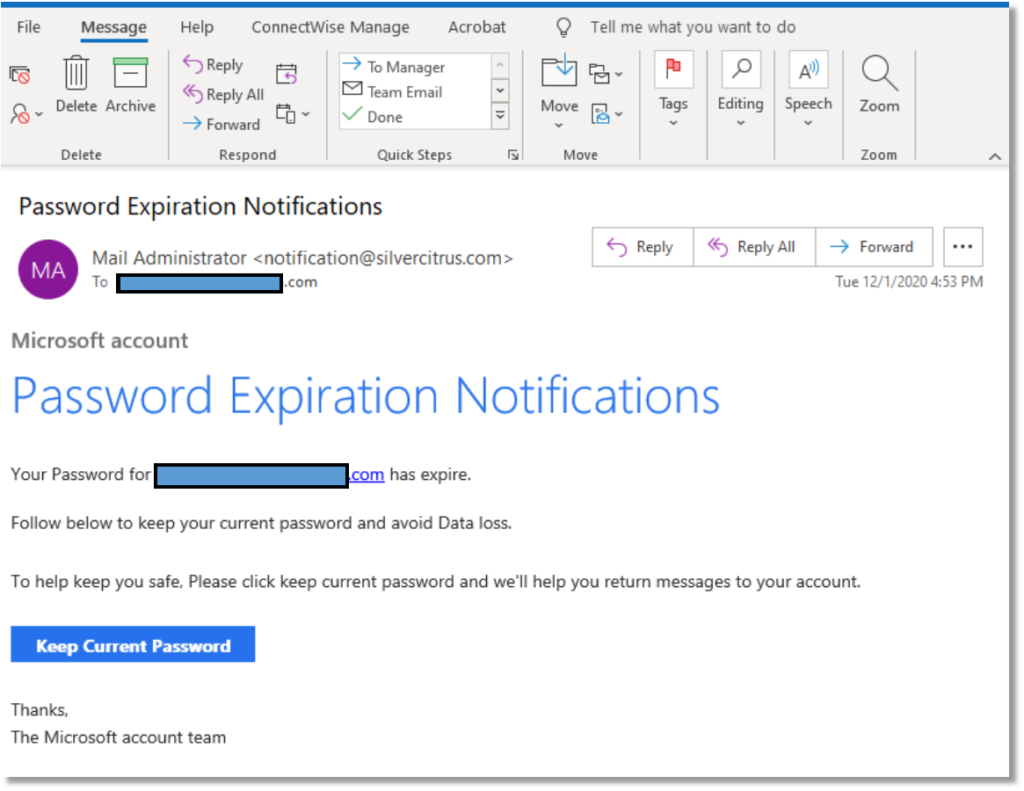
- Provide Employee Training: Educate your employees about the importance of network security and best practices. Human error is a common factor in security breaches, so a well-informed workforce is a critical line of defense. Conduct regular training sessions to keep employees updated on the latest security threats and ensure they understand their role in maintaining a secure network environment.
A well-managed corporate computer network is essential for business success in the digital age. By following these best practices, business owners can build a secure, reliable, and efficient network infrastructure that supports their organization’s growth and innovation. Regularly assess and update your network to stay ahead of emerging threats and technological advancements, ensuring that your business remains competitive and resilient in today’s dynamic business landscape.
If your company would like more information about Network Best Practices, would like a Free Network Assessment or how to keep your network running at its best, contact Infinity Networking today!