The most common way that business and personal accounts become compromised is through phishing and spear phishing attacks. These attacks are more common recently with the pandemic forcing people to work from home and often separated from their company’s established cybersecurity protocols. The majority of computers these days have some form of antivirus and firewall protection, but human nature is often the weakest link in the security wall. In this blog post, you will learn how to recognize a fake email and how to avoid becoming the victim of a phishing scam.
What is Phishing?
A phishing attack is an email sent by a bad actor that appears like a legitimate notice or request for information. Most of the time they appear as if they originate from Microsoft, Apple, a well-known bank, Paypal, Amazon, etc. The phishing email often announces a new feature or a request for the user’s information that requires the user to log into their account using their credentials. The links from these phishing emails lead to a very convincing (yet fake) website that appears legitimate. But when the user enters their information, the victim has essentially given the scammer their private credentials. There have been numerous high profile celebrities and politicians that have fallen for these scams.
—
The Impulsive Clicker
Most people, especially in a business environment, gets 10’s if not 100’s of new emails each day. We have become rather proficient at sorting through the spam and keeping the important ones. However, since we are dealing with a large volume of emails at one time it is easy to just open one from a familiar source and click on the link. Especially if the email is from a popular vendor or B2B company.
Phishing attacks take advantage of our human nature to be in a hurry and not carefully read what we are opening.
—
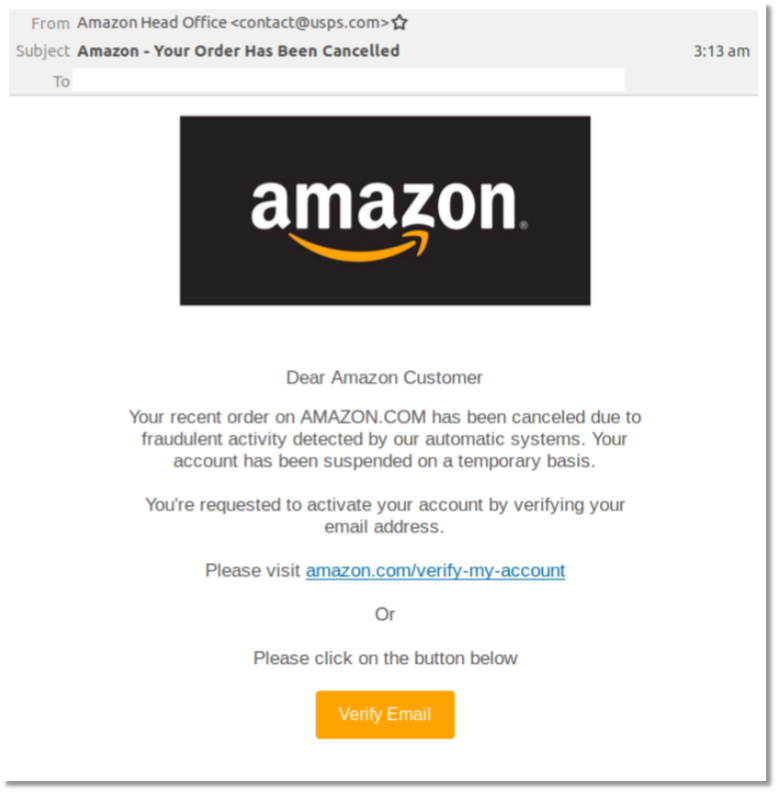
Advanced Tactics – Spear Phishing
Phishing attacks have now evolved into a more sophisticated form called ‘spear phishing’. Someone who receives an account password reset email from eBay, but who never uses eBay will know right away that the email is not legitimate. But if the scammers can get a little more information, for example the name of a co-worker at the company, they can send their phishing email that looks like it comes from someone familiar, bypassing that first line of mental defenses. The more the scammers know about a recipient; their co-workers, vendors, clients, account numbers, etc. the more convincing they can make the phishing emails appear. This is called spear phishing.
Phishing in Other Ponds
Phishing attacks are now common in other communication media as well including text messages, phone calls and search engines.
Arming Yourself
How do you avoid being the victim of a spear phishing attack? There are few tactics that everyone needs to know.
1) Slow down and stop being the ‘impulsive clicker’. Look at not only the sender’s name, but also the email address. At the top of the email, you will see the name of the person and then their email address between < and >. For example John Smith <[email protected]>. If the address looks like this John Smith <[email protected]> then that should raise a big red flag!
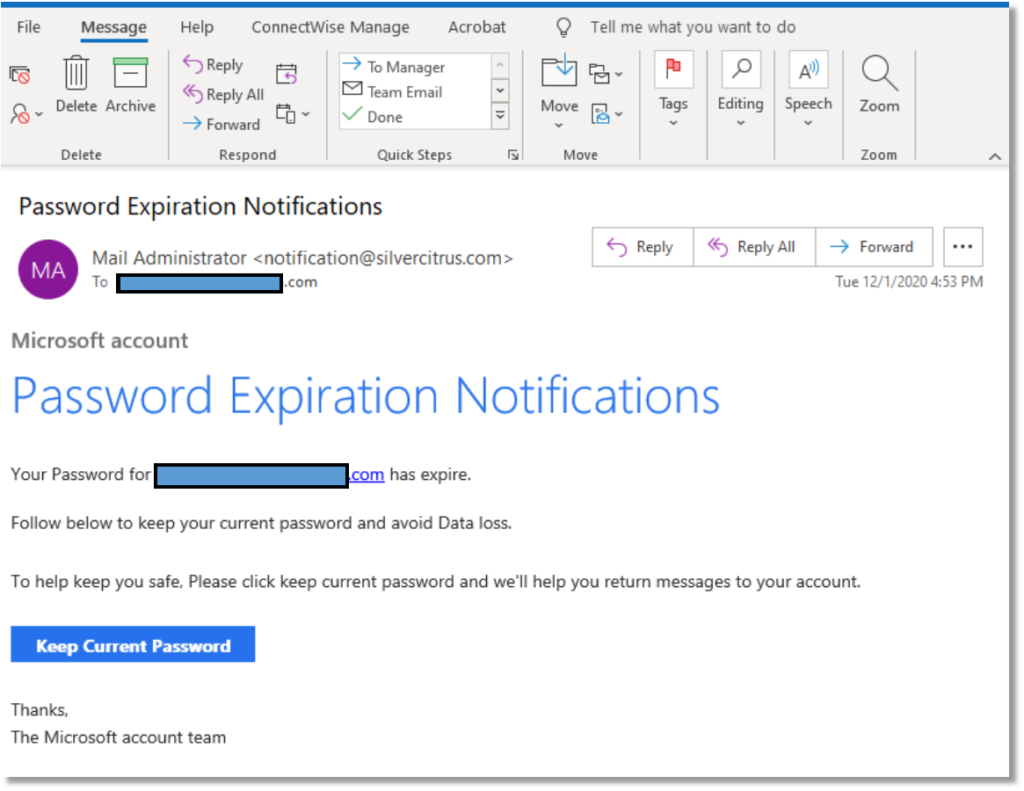
2) If you get an email that looks like it is from a well-known organization, look for misspellings and poor grammar. Also, use your mouse to hover over any hyperlinks (do not click on them). Most of the time, fraudulent links will be obvious when you look at their address in the bar at the bottom. See example below:
This is supposedly from the “Microsoft Account Team”. Notice the inconsistent capitalizations, the incorrect usage of ‘expired’ and the email address it is sent from – doesn’t look like Microsoft.
When the mouse is hovered over the “Keep Current Password” box, this is the link that appears:
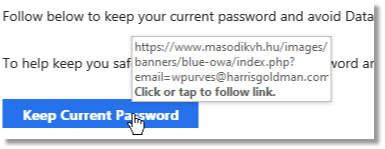
Doesn’t look like it directs to Microsoft…
3) Employing a robust enterprise-grade email filter is also a good way to avoid phishing attacks. Services like Barracuda Cloud Control have built-in mechanisms to block these types of scams.
4) One of the most effective IT security measures a company can make is to invest in regular Security Awareness Training. Almost all compliance regulations require companies to keep their employees updated and tested against the latest cyber threats on a regular basis.
For more information about what you can do to prevent a successful phishing attack, including a good email filtering service like Barracuda Cloud Control or regular Webroot Security Awareness Training, contact Infinity Networking for a FREE TRIAL of these services.
Click here for more information about Infinity Networking’s Cybersecurity solutions
—




Very informative post with plenty of practical details & tips. This was time well spent.